
With the ups and downs of the crypto currencies One trend remains constant: New investors keep pouring into the crypto exchanges. Many are investing in a digital currency for the first time – and are not aware of the associated security risks.
Methods are repeatedly discussed in the Darknet and relevant forums to get to the digital coins. Here are the four most common attack vectors used by hackers as well as tips and recommendations on how to protect e-wallets.
More on the subject
- Overview of crypto news: The t3n news blog about Bitcoin and Co.
Eavesdropping: reverse proxy -Phishing
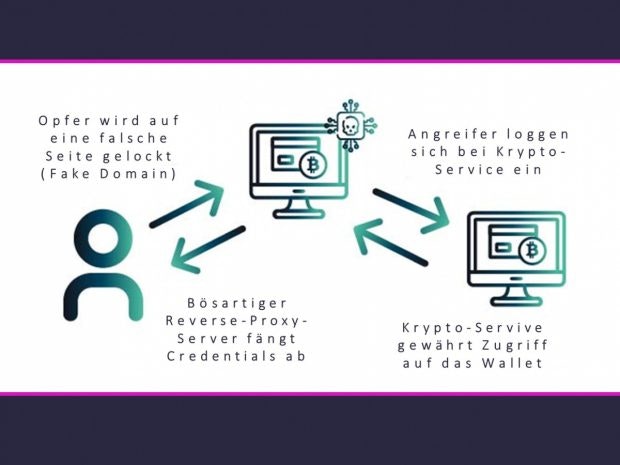
Phishing is the Scam to intercept sensitive information and crack accounts. It is no different with crypto wallets. However, a special shape is used here. Reverse proxy phishing is a type of domain spoofing man-in-the-middle attack. Similar to eavesdropping in a spy film, attackers secretly eavesdrop on the traffic between two unsuspecting parties.
This method is popular because it allows cyber criminals to cheat two-factor authentication (2FA). The authentication process is particularly effective in preventing third parties from hacking into someone else’s wallet using leaked or stolen login data. Reverse proxy phishing therefore takes a little detour. A phishing e-mail lures the owner of an e-wallet to a wrong page that looks very similar to the original page. The problem: the fake domain is hosted on a malicious reverse proxy server. This switches itself between the server of the victim and the server of the legitimate login page. Hence the name “Man in the Middle” (MitM). Once positioned, the reverse proxy server can observe the entire data traffic.
(Graphic: Digital Shadows)
Next, it gets the legitimate login page and loads a copy for the victim. Stolen SSL certificates ensure that the victim’s browser does not become suspicious. Unsuspecting, the owner logs into his e-wallet – as prescribed by 2FA with both credentials. The malicious server gratefully accepts it, logs on to the legitimate login page and empties the e-wallet.
What to do?
Is it switched in between, the reverse proxy server is not so easy to shake off. 2FA with a security key (hardware token) can usually ward off such attacks. However, such tokens are rarely used.
The best defense against phishing: Don’t click on suspicious emails and links! Even if it has to be quick, it is worth taking a second look at the website and URL. Scammers are terrifyingly good at recreating legitimate sites. It is best to navigate to your e-wallet directly via the provider’s homepage – and never via e-mails or third-party sites.
Cryptojacking: Hijacked computing power
In cryptojacking, attackers target the processing power of a computer. The CPU is hijacked and used by botnets to mine cryptocurrency. The computers become infected via malicious links and turn into externally controlled zombies. The mining malware runs in the background and is sometimes not noticed for years – not even by antivirus software.
Web-based cryptojacking uses scripts that run on a website or domain. If you land on the infected host while surfing the web, mining takes place via the browser. In 2017, a Starbucks branch Wi-Fi network was hacked. Guests who went online via the free WiFi also mined crypto currencies on the side
What to do?
There are definitely signs of hidden mining. If the CPU usage of your computer increases rapidly, if it is louder than usual or if it starts extremely slowly, this may be due to cryptojacking. Browser plugins such as Adblock and Minerblock can protect against web-based cryptojacking. Otherwise, the following also applies here: Stay away from suspicious-looking e-mails and be careful when using public WiFi.
Clipping: redirecting transactions
Clipping takes place during the transaction from one e-wallet to the other. A backdoor Trojan is used to smuggle in special malware, the cryptocurrency clipper, which is hidden in popular apps (such as a PDF reader), in mobile phone games and, more recently, in Covid-19 trackers.
As with bank transfers, a recipient or the wallet address must be specified in the form of a code for cryptocurrencies. When entering the data, many users use the copy & paste function for the sake of simplicity. Who wants to memorize rows of numbers for a long time and type them in by hand? This is what the clipper has been waiting for. He fetches the e-wallet address from the clipboard and replaces it with the attacker’s wallet address. When inserting it into the transfer form, the exchange is hardly noticeable and the Bitcoin wander unhindered into the hands of others.
What to do?
Dusting: lay a track and follow
Dusting cryptocurrencies is a bit more complex. The crypto wallet is deanonymized. Tiny amounts of crypto dust are sent to a wallet to be tagged. Attackers can follow this trail, observe transactions and analyze the addresses on the blockchain. In the analog world, it would be like putting a tracker on a bill and then smuggling it into someone’s wallet. As soon as you pay with the marked bank note, you can find out your identity and e-wallet.

(Screenshot: Digital Shadows)
Successful dusting is often just the starting point for sophisticated spear phishing campaigns. Attackers can pretend to be real investors to trading platforms and crypto exchanges and request a new transfer of allegedly not received Bitcoin. Equipped with a wallet address and transaction number, the chances of success are significantly higher to get away with it.
What to do?
The best way to prevent dusting attacks is for generate a new wallet address for each transaction. Some wallets also allow you to parse funds or mark smaller, suspicious deposits and block them for transactions. Or to stick with the comparison above: You avoid paying with banknotes that suddenly appear in your wallet. If the “dust” is not moved, it cannot be tracked. In general, investors should watch transactions closely. Wallet apps help to keep track and report even the smallest amounts.
Conclusion
Man-in-the-middle, hijacking, clipping and dusting – none of the techniques is really new. They were simply aimed at a new target. The more cryptocurrency becomes mainstream, the more lucrative attacks on digital wallets and cryptomining become. Investors have no choice but to keep up to date with current scams and attack techniques. Staying vigilant can be exhausting, but it is still the safest way.




